Hackers Using PrivateLoader PPI Service to Distribute New NetDooka Malware
A pay-per-install (PPI) malware service known as PrivateLoader has been spotted distributing a “fairly sophisticated” framework called NetDooka, granting attackers complete control over the infected devices.
“The framework is distributed via a pay-per-install (PPI) service and contains multiple parts, including a loader, a dropper, a protection driver, and a full-featured remote access trojan (RAT) that implements its own network communication protocol,” Trend Micro said in a report published Thursday.
PrivateLoader, as documented by Intel 471 in February 2022, functions as a downloader responsible for downloading and installing additional malware onto the infected system, including SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.
Featuring anti-analysis techniques, PrivateLoader is written in the C++ programming language and is said to be in active development, with the downloader malware family gaining traction among multiple threat actors.
PrivateLoader infections are typically propagated through pirated software downloaded from rogue websites that are pushed to the top of search results via search engine optimization (SEO) poisoning techniques.
“PrivateLoader is currently used to distribute ransomware, stealer, banker, and other commodity malware,” Zscaler noted last week. “The loader will likely continue to be updated with new features and functionality to evade detection and effectively deliver second-stage malware payloads.”
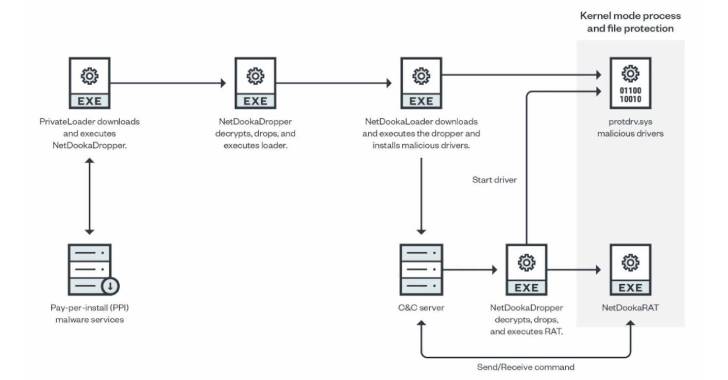
The NetDooka framework, still in its development phase, contains different modules: a dropper, a loader, a kernel-mode process and file protection driver, and a remote access trojan that uses a custom protocol to communicate with the command-and-control (C2) server.
The newly observed set of infections involving the malware framework commences with PrivateLoader acting as a conduit to deploy a dropper component, which then decrypts and executes a loader that, in turn, retrieves another dropper from a remote server to install a full-featured trojan as well as a kernel driver.
“The driver component acts as a kernel-level protection for the RAT component,” researchers Aliakbar Zahravi and Leandro Froes said. “It does this by attempting to prevent the file deletion and process termination of the RAT component.”
The backdoor, dubbed NetDookaRAT, is notable for its breadth of functionality, enabling it to run commands on the target’s device, carry out distributed denial-of-service (DDoS) attacks, access and send files, log keystrokes, and download and execute additional payloads.
This indicates that NetDooka’s capabilities not only allow it to act as an entry point for other malware, but can also be weaponized to steal sensitive information and form remote-controlled botnets.
“PPI malware services allow malware creators to easily deploy their payloads,” Zahravi and Froes concluded.
“The use of a malicious driver creates a large attack surface for attackers to exploit, while also allowing them to take advantage of approaches such as protecting processes and files, bypassing antivirus programs, and hiding the malware or its network communications from the system.”
